As cyber-attacks increase in frequency and potential damage, now more than ever, it has become critical that businesses of all sizes, as well as consumers, take online security seriously. Data breaches are happening more frequently, and at record-breaking rates. The Identity Theft Resource Center (ITRC) reported that in 2016, there were 4,149 reported incidents worldwide, 1,093 of which were in the United States, representing a massive spike of 40% compared to 2015.
Every company, regardless of its size, could benefit from awareness of their cyber risks, executing a current state assessment of their environment, identifying gaps, and establishing a plan to remediate them. The keys to protecting your organization against cyber-attacks are awareness and preparation. Our intent is to shed some light on emerging risk which your business should prepare for, as well as reoccurring issues that continue to plague companies, and to offer potential solutions to address these risks .
How Data Breaches Happen
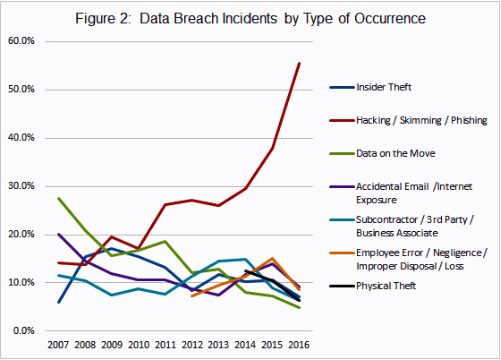
Since 2007, the ITRC has been identifying and tracking data breach incidents into “type of occurrence” categories. (see chart below) For the 8th consecutive year, the leading cause of data breach incidents in 2016 was hacking/skimming/phishing attacks, which accounted for 55.5% of the overall number of attacks.
How Businesses Can Protect Themselves from Data Breaches
For Small to Medium Size Businesses:
Often small to medium size businesses fall under the false impression that cyber attackers only target larger sized companies, where there are potentially bigger payouts. However, this is simply untrue. Small to medium sized businesses are victims of nearly half of all cyber-attacks since they are much easier to penetrate as they typically don’t have cyber security solutions on the scale that larger organizations do. No matter the size of your IT infrastructure, cyber security should always be a top priority. In addition to protecting your organization against hacking/phishing attacks, we recommend that company data be moved to the cloud to take advantage of cyber insurance.
For Large Corporations:
Many CEOs and senior executives often inquire how to “solve” the risks of a cyber-attack. Instead organization and their leaders need to acknowledge that cybersecurity is an ongoing battle as new assets and attack techniques continue to evolve. For larger corporations to stay ahead of potential threats, cybersecurity should be a consistent item on executive’s agendas.
The following critical questions should regularly be addressed:
- How is our approach to cybersecurity evolving and are our business processes being adjusted accordingly? Who is responsible for this?
- Which assets are most critical in the event of an attack and what are their values at stake?
- What efforts, processes, and tactics are in place to protect our critical information assets?
- How does our cybersecurity approach compare to that of our competitors and industry best practices?
- How are we managing our outside relationships to ensure mutual security of information?
Organization of all size typically approach cybersecurity by establishing defense around its perimeter. However, the harsh reality is that a determined attacker will most likely find a vulnerable access point. Regardless of the size of your organization, awareness and preparation are critical aspects of cyber security. To start protecting your organization, we recommend the following:
- Regularly update operating systems on all devices within your company, making sure to update whenever new security patches are released.
- Establish a strong password policy for all employees
- Secure all mobile devices within your company by enabling “remote wipe” capabilities for phones and tablets and “kill switch” to allow only the device owner to perform a reboot,
- Utilize virtual private network (VPN) to encode your internet connection and protect online shared data from third parties.
- Implement a company-wide rule that a download should not be executed if the recipient doesn’t know the sender.
- Keep your employees in the know about cyber security by educating and training them against potential cyber threats.
Recruiting Top IT Security Talent Despite the Shortage of Skilled Professionals
IT security recruiting and staffing has been a long-standing challenge within the industry. Companies understaffed within their IT departments often turn to InSource to find qualified, skilled IT talent to help implement and maintain security operations and identity management solutions to help guard their organization against potential data breaches. Our experienced recruiters follow a rigorous candidate screening process that leverages our decades of experience to match the right candidate to your company’s needs, helping to advance your organization, improve efficiency and increase cyber security.
Let InSource Help Strengthen Your Organization’s Protection Against Cyber Attacks
Since most small to medium sized businesses don’t have the resources to deploy and maintain their own cybersecurity systems effectively, they need a customizable solution that is simple to implement, run and monitor, with automated controls, threat identification, and responses in place. Through our partnership with Okta and ServiceNow, Insource delivers world-class identity management and security operation solutions. These offerings can work as stand-alone cloud-based security systems or can prove a valuable expansion of your existing ServiceNow platform. InSource, a ServiceNow Master Partner, works closely with ServiceNow, an industry leader, to implement security measures such as security, strong encryption, making auditing and system logs available, roles and responsibilities based privilege provisioning, etc.
Act now to help protect your organization from potential cyber threats, contact us today to discover how our identity management and security operations solutions can help improve your business’ cyber security. Request a demo or contact one of our professionals today!
Resources:
https://www.idtheftcenter.org/notified
https://www.csoonline.com/article/3150255/5-cybersecurity-trends-to-watch-for-2017.html